Bastion
Bastion
Takes all the complexity on itself!
SSH server with role-based mandatory access model using zero trust principles.
Designed for secure infrastructure access through centralized control and SSH session auditing. Unlike traditional SSH servers, Bastion focuses on user identification, temporary certificates, and role-based access model.
Available on Team
Core principles
- Mandatory model
- Role-Based Access Control, RBAC — access to SSH servers is managed through roles and policies, not manually through authorized_keys files.
- Zero trust
- The zero trust principle. Checks not only user credentials, but also context: Who is requesting access? Which server and for what purpose? What are the session parameters (time, source, MFA policy)?
- Passwordless authentication
- Passwordless — instead of static passwords, PKI certificates that automatically expire are used in addition to SSH keys.
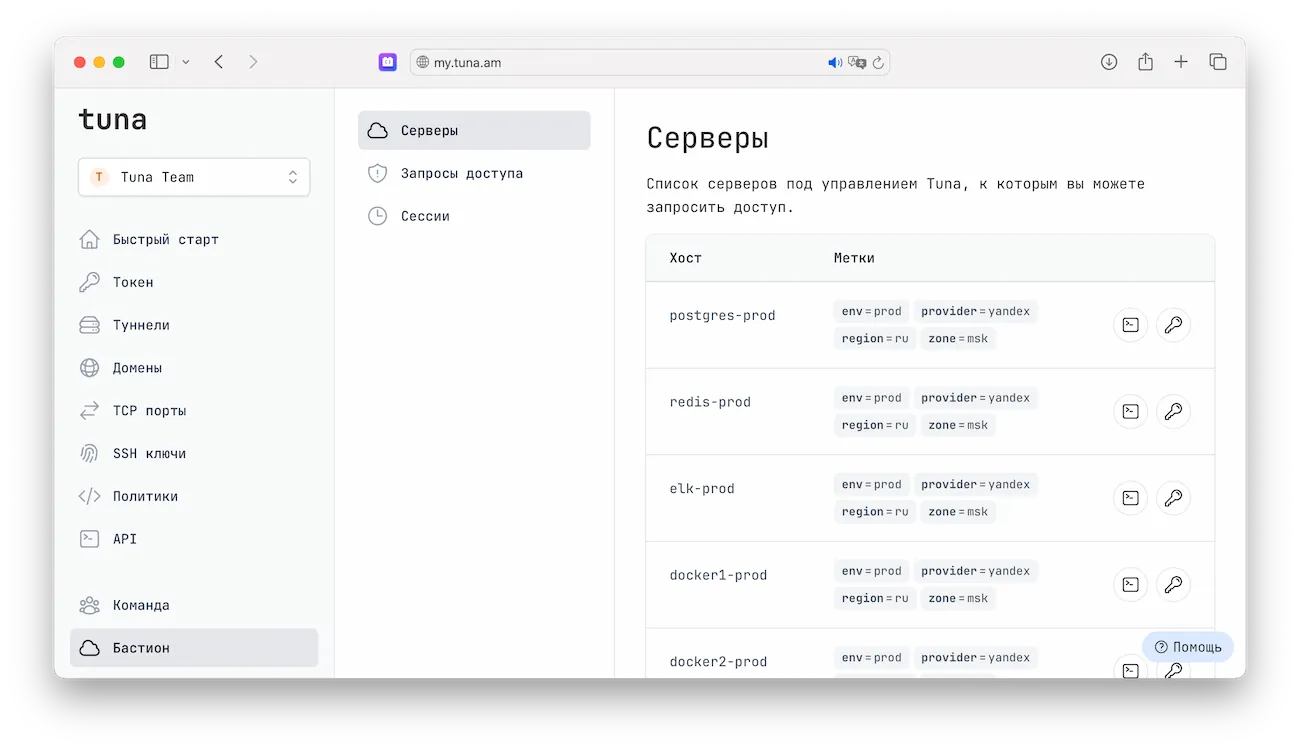
What is a bastion in the context of SSH access?
Instead of traditional SSH access ssh user@host based on passwords or RSA keys, users authenticate through our tuna client on our portal.
Then certificate-based authentication works on the bastion server. This is a standard OpenSSH feature, it is the most secure of all, but historically it is the most difficult to configure. And this is where we take all the complexity on ourselves, leaving you only with security!
After authorization on the portal, the client generates RSA keys and transmits the public part to the API for delivery to bastion servers. The client also generates a temporary PKI certificate which is signed by CA in the Tuna portal. With the RSA key and certificate, you connect to the server, the server checks that the certificate is valid, signed by the correct CA, and the user for whom the certificate was issued has sufficient access rights considering roles and policies.
Bastion servers in turn also have temporary certificates signed by CA, and when establishing a connection, the client also checks the server's validity in CA: this way you can be sure that your server is exactly your server, not something fake.

As a result, we know nothing about the private keys of servers and clients, they are generated and stored locally, which means we have no way to connect to your infrastructure (as well as attackers in case of hypothetical leaks from us). We act as a third party — the CA keeper who signs certificates and authenticates the user.
Reviews about Bastion
How does it work?
- 1
You run tuna-bastion on your server and register it in Tuna API. A pair of RSA keys and a 30-day certificate are generated, signed by a CA allocated to the team in Tuna API. The private key is stored locally and is not transmitted anywhere, Tuna API doesn't know it, i.e. we have no access to your servers.
- 2
In the my.tuna.am control panel, you create a role describing the access model and apply it to the desired user.
- 3
The user runs the command tuna bastion login username. A pair of RSA keys and a 12-hour certificate are generated, signed by a CA allocated to the team in Tuna API, similar to the server. But this only happens if the user has sufficient rights to connect with such a login.
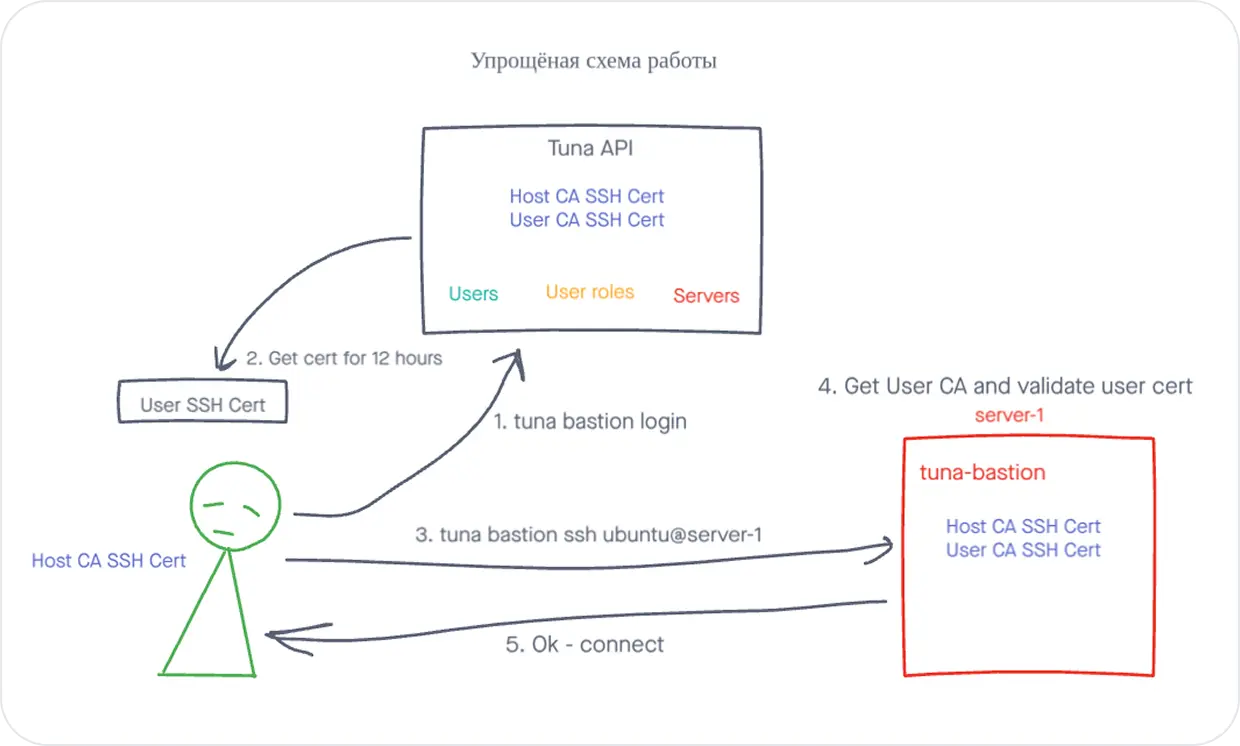
- 4
The user runs the command tuna bastion ssh username@hostname, and if their certificate is valid, the server certificate is valid, the user has sufficient rights and no restrictions are imposed, then the session is established.
- Read documentation →
 TUNA — platform for developers
TUNA — platform for developers TUNA
platform for developers
TUNA
platform for developers
 TUNA — platform for developers
TUNA — platform for developers TUNA
platform for developers
TUNA
platform for developersPricing
Get 2 months free with annual subscription
Hobby
- 1 HTTP tunnel
- 30 minutes of operation
- Dynamic subdomains
- 1 project
- 5 environments per project
- 5 configs per environment
- 1 webhook
- 1 project
- 7 days storage
Free
InstallDeveloper
- 5 tunnels simultaneously
- 10 subdomains in tuna.am zone
- 1 static port
- 1 own domain
- No time limit
- All tunnel types
- 10 projects
- 10 environments per project
- 10 configs per environment
- 3 monitors (watch)
- 10 webhooks
- 1 project
- 30 days storage
5 USD /month
50 USD /year
BuyTeam
- 10 tunnels simultaneously
- 10 subdomains in tuna.am zone
- 10 own domain
- 5 static ports
- Own domain zones
- Traffic policies
- IP access policies
- 20 projects
- 20 environments per project
- 20 configs per environment
- 5 monitors (watch)
- 10 webhooks
- 20 projects
- Unlimited storage
- 200 nodes per team i
10 USD /month
100 USD /year
Buy
What's included in the plan
- Traffic policies i
- IP access policies
- Own domain zones (wildcard)
- IP address hiding in dynamic subdomains
- 10 tunnels simultaneously
- 10 own domains
- 5 static ports
- No time limit
- HTTP tunnels
- TCP tunnels (RAW, SSHd, Postgres, Redis)
- SSHd tunnels (built-in SSH server)
- Trigger tunnels (Webhook or Email)
- 10 subdomains in tuna.am zone
- Multiple regions
- Dynamic subdomains
- End-to-end encryption
- Let's Encrypt SSL/TLS certificates
- HTTP / Postgres / Redis requests inspector
- Basic authentication
- Access restrictions by IP/Api-Key/User-Agent
- Rate limiting
- CORS automation
- Websocket and Server-Sent Events (SSE) support
- Built-in file server
- WebDAV server
- Service creation management (background operation)
+1 Additional license
$2 /month
- +1 active tunnel
- +1 subdomain in tuna.am zone
- +1 own domain
- +1 static port
What's included in the plan
- TCP tunnels (RAW, SSHd, Postgres, Redis)
- SSHd tunnels (built-in SSH server)
- Trigger tunnels (Webhook or Email)
- No time limit
- 5 tunnels simultaneously
- 10 subdomains in tuna.am zone
- 1 static port
- 1 own domain
- HTTP tunnels
- HTTP / Postgres / Redis requests inspector
- Multiple regions
- Dynamic subdomains
- End-to-end encryption
- Let's Encrypt SSL/TLS certificates
- Basic authentication
- Access restrictions by IP/Api-Key/User-Agent
- Rate limiting
- CORS automation
- Websocket and Server-Sent Events (SSE) support
- Built-in file server
- WebDAV server
- Service creation management (background operation)
+1 Additional license
$1 /month
- +1 active tunnel
- +1 subdomain in tuna.am zone
- +1 own domain
- +1 static port
What's included in the plan
- Multiple regions
- 1 HTTP tunnel
- Dynamic subdomains
- 30 minutes of operation
- End-to-end encryption
- Let's Encrypt SSL/TLS certificates
- HTTP requests inspector
- Basic authentication
- Access restrictions by IP/Api-Key/User-Agent
- Rate limiting
- CORS automation
- Websocket and Server-Sent Events (SSE) support
- Built-in file server
- WebDAV server
- Service creation management (background operation)
What's included in the plan
- 1 project
- 5 environments per project
- 5 configs per environment
- Secrets generator
- Change history
- Secrets synchronization across environments
- Compare secret values across environments
- Hidden secrets
- IP address access
- Service keys for specific configuration access
What's included in the plan
- 10 projects
- 10 environments per project
- 10 configs per environment
- 3 monitors (watch)
- Automatic application restart on secret change (watch)
- Secrets generator
- Change history
- Secrets synchronization across environments
- Compare secret values across environments
- Hidden secrets
- IP address access
- Service keys for specific configuration access
What's included in the plan
- 20 projects
- 20 environments per project
- 20 configs per environment
- 5 monitors (watch)
- Automatic application restart on secret change (watch)
- Secrets generator
- Change history
- Secrets synchronization across environments
- Compare secret values across environments
- Hidden secrets
- IP address access
- Service keys for specific configuration access
What's included in the plan
- 1 webhook
- View HTTP requests
- View Email
What's included in the plan
- 10 webhooks
- View HTTP requests
- View Email
What's included in the plan
- 10 webhooks
- View HTTP requests
- View Email
What's included in the plan
- Password storage using zero-knowledge model
- Secrets type separation
- TOTP support
- External sharing capability
What's included in the plan
- Password storage using zero-knowledge model
- Secrets type separation
- TOTP support
- External sharing capability
What's included in the plan
- Shared catalogs
- Password storage using zero-knowledge model
- Secrets type separation
- TOTP support
- External sharing capability
What's included in the plan
- 200 nodes per team i
- Zero-Trust SSH access to servers
- Mandatory (RBAC) access model
- Authentication using temporary RSA keys and PKI certificates
- Audit and observability (coming soon)
- SSO integration (coming soon)
What's included in the plan
- Traffic policies i
- Number of gateways is limited by the limit on static domains and subdomains in the tuna.am zone
What's included in the plan
- Role-based access control (RBAC)
- Event audit
- Invoice payment (RU)
What's included in the plan
- 1 project
- 7 days report storage
- Screen recording
- Browser console
- Network requests
- DOM snapshot
- Report comments
What's included in the plan
- 30 days report storage
- 1 project
- Screen recording
- Browser console
- Network requests
- DOM snapshot
- Report comments
What's included in the plan
- 20 projects
- Unlimited report storage
- Screen recording
- Browser console
- Network requests
- DOM snapshot
- Report comments

 How to start?
How to start?
Start with installing and initial setup of the client - it will take no more than a minute
 Frequently asked questions about Bastion
Frequently asked questions about Bastion
Currently, Bastion is only available on the Team plan.
No, the number of Bastions can be unlimited.
Ways to work with Bastion with examples are described in detail in the corresponding section of our documentation.
Still have questions? Email us at info@tuna.am or ask a question in our Telegram community.

Unified platform for:
- accelerating development
- simplifying team collaboration
- improving security
- cost optimization
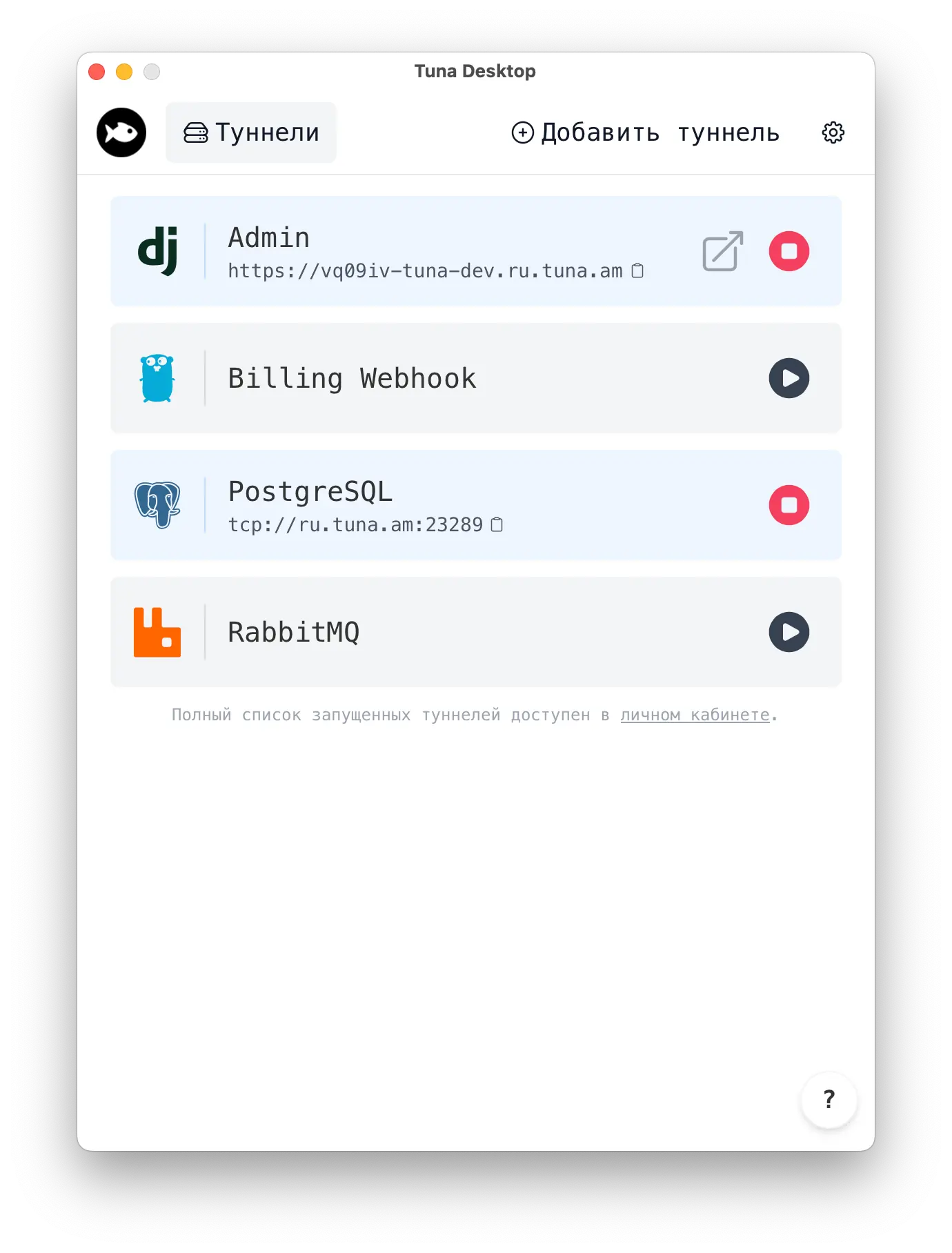
Tuna Desktop
A new way to manage tunnels without the console. Install on Windows, MacOS or Linux and get started in seconds.
Install